Avast Security (for Mac) delivers effective malware protection along with unusual bonus features. Phishing protection only works well in Chrome and Firefox, but this free utility is still worth a. Need premium Mac antivirus protection? Say hello to Avast Security Pro. Avast Security Pro includes all the malware-crushing moves of its free little brother, along. Avast Pro Antivirus has a strong feature list with good scores for protection and usability, though it may cause your computer to run slower. Avast forums indicated that there is a bug in this update, after three reboots my computer got completely stuck when trying to access the 'repair' function so I phoned Avast tech # given on bottom. Though Sophos does offer a good free version of its software, Avast Free Mac Security edges it out as the best free antivirus software for macOS. In security lab tests, Avast detected 99.9 percent.
Published February 24th, 2015 at 12:47 PM EDT , modified March 5th, 2015 at 10:28 AM EDT
The security community is ablaze with news of Superfish being pre-installed on some Lenovo computers. The primary issue concerning experts is that Superfish replaced SSL certificates, used for ensuring secure connections on the internet, with its own certificates. It turns out that the same behavior is being exhibited by software that many people are inclined to trust: Avast’s anti-virus software!
Replacing SSL certificates is a significant security issue. The lock icon shown by browsers when the user is connecting to an “HTTPS” site is an indication that the connection is being secured, using a form of encryption that relies on an SSL “certificate” issued by a trusted certificate authority. So, when you connect to your bank’s website, for example, a certificate is used to encrypt all data sent between your browser and the bank site. This protects you from snoops, who cannot see any potentially sensitive data being transmitted.

What Superfish has done is replace these certificates with one of its own, which gives the software the ability to intercept any data being sent to or from such a secure site. This is what security experts call a “man-in-the-middle attack,” meaning something or someone that interjects itself between two parties attempting to have secured communications. It should be immediately obvious that this is a Very Bad Thing.
Avast For Mac Review
Surely this kind of thing could only be done by unethical hackers, right? I mean, Superfish is essentially adware, and in my opinion has now crossed the line into malware territory. So we shouldn’t be surprised at its misbehavior. No legitimate software would ever behave this way, would it?
Don’t be too sure. I received an e-mail from a reader yesterday asking why he was getting an error in Chrome complaining that his connection to Google was not private. The error message pointed the finger at a certificate issued by a certificate authority named “Avast untrusted CA.”
Some testing this morning showed that Avast is replacing Google’s certificate with one of their own. On my test system, though, the Avast certificate was trusted. (I’m guessing the certificate on the affected reader’s system was outdated, and had not been properly updated for some reason.)
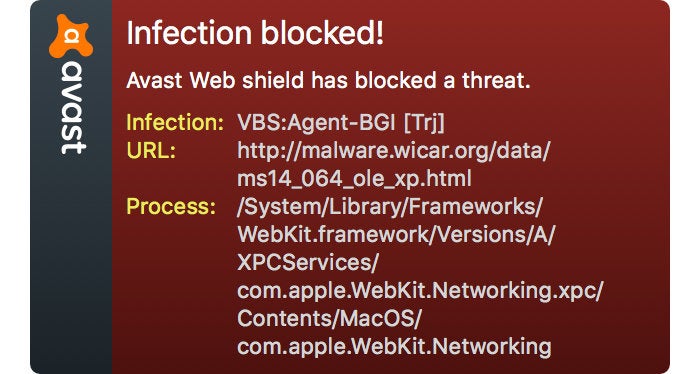
As can be seen from the screenshot, the certificate claims to be for Google, but was not issued by the authority that Google actually uses (GeoTrust Global). This means that Avast has complete control over the connection between the browser and Google, and has the power to intercept – or even modify – any data being transmitted.
Okay, who cares, right? I mean, sure, there are some potential privacy issues involved there, but in reality, most people don’t care much if someone’s monitoring their searches. Those who do are probably using a search engine like DuckDuckGo, rather than Google, anyway.
Unfortunately, this issue isn’t limited to Google. Suppose, for example, that you go to the Bank of America site to transfer some funds or pay a bill. As with Google, and as would happen with any other secure site, it turns out their certificate gets replaced with the Avast certificate. I doubt anyone needs me to lecture them on the potential security issues involved in having a third-party watching their banking transactions without permission!
This is an extremely serious issue, but surprisingly, it apparently isn’t new! Searching the web for “Avast untrusted CA” or “Avast trusted CA” shows that people have been aware of this on a small scale for some time. On Avast’s own forums, questions about this are treated as bugs – not because of the potential security issues involved, but because of whatever has caused the user in each case to become aware of the problem, such as the error message that brought this matter to my attention.
Avast For Mac Free Download
It’s unlikely that Avast is using the power to snoop on your communications for malicious purposes. I imagine that they are using this power to monitor secured communications for possible malware. For example, Avast is probably intercepting e-mail being transmitted securely between your mail server and your e-mail client so that it can be scanned for attached malware.
However, the issue here is one of trust. Should you trust Avast with this kind of access to your private information? Avast has essentially chosen to hijack your web browser’s security without your permission, inserting itself as a silent watcher into all your secure communications. Worse, Avast has a history of sometimes showing untrustworthy behavior in the past, such as including an adware component in their avast! Online Security browser extension. This is not behavior that should be tolerated, and I strongly recommend uninstalling Avast immediately.

Even if you trust Avast 100%, however, an added issue is the potential for new security risks. In the case of Superfish, for example, security researcher Robert Graham was able to crack the certificate being used by Superfish, due to a poor certificate password, and could have then launched his own attacks on unsuspecting users using that certificate. If Avast’s security is at all sloppy, their certificate could cause security issues that would not exist if Avast did not tamper with certificates.
To be fair to Avast, it’s entirely possible they are not alone. Other anti-virus software could be behaving in exactly the same way. A quick test of a number of other free Mac anti-virus apps this morning did not uncover any, but I did not test every anti-virus app out there by a long shot. Still, any other anti-virus software that might be doing this should also be avoided.
To determine whether your system might be affected by such an issue, go to www.google.com in Safari. There should be a lock or “https” icon in the address bar, indicating that the connection to Google is secure. Click that icon, then click the Show Certificate button in the sheet window that drops down. The certificate should be issued by Google Internet Authority, which in turn falls under the authority of GeoTrust Global. If you see anything different, you may be the victim of a man-in-the-middle attack. This could be the result of other anti-virus software, or could be due to something else, such as a compromised network connection.
Updates
Thursday, March 5, 2015 @ 9:45 am EST: After taking some considerable heat from some folks – including an Avast representative – in the comments below, it turns out that the situation is even worse than I initially realized. Avast is replacing certificates with its own without bothering to check the validity of those certificates!
So what does this mean? Suppose that there’s a malicious site out there that uses HTTPS, in an attempt to trick the user into thinking the site is legit. (Or perhaps a formerly legit site has changed hands and become malicious.) Then suppose the malicious intent of the site is discovered, and the certificate is revoked. Your web browser should warn you that the site is not trustworthy if you try to go there.
If you happen to have Avast installed, no such luck. Because Avast will replace the site’s revoked certificate with Avast’s own legitimate certificate, eliminating the error and allowing you to navigate to a site that you shouldn’t!
Nobody needs to take my word for this. It’s trivial to test it if you have Avast installed, and have not disabled Avast’s HTTPS scanning: just navigate over to revoked.grc.com, a site designed for testing purposes that uses a revoked SSL certificate. As you can see from the screenshot at right, the site opens just fine, using Avast’s replacement certificate.
You may say that my hypothetical situation above is unlikely to happen. That’s true. However, the news in recent years has been frequented by stories about SSL certificate theft. Hackers can use stolen certificates to execute real man-in-the-middle attacks, tricking your browser into believing that it is visiting a legit site when it isn’t. Stolen certificates are generally revoked after the theft has been discovered, but this vulnerability in Avast will allow those certificates to continue to work.
I’ve had some tips that other anti-virus apps behave the same way, in particular BitDefender, Kaspersky and ESET. However, I was unable to bypass the revoked certificate using Kaspersky, and ESET’s Mac software appears not to do any kind of HTTPS scanning as far as I can tell. The jury is still out on BitDefender, as I haven’t yet been able to download a trial version. (I haven’t received the e-mail I need in order to download the trial software.) I’ll update later, after I’ve tested BitDefender.
This is precisely the kind of security issue that tampering with HTTPS can result in, and is exactly why it should not be done. Case closed.
Thursday, March 5, 2015 @ 10:30 am EST: I finally got a copy of BitDefender’s Mac anti-virus software, and it appears not to be doing any HTTPS scanning. It may do that on Windows – I have to rely on third-party reports there – but as best I can determine, it doesn’t have this problem on the Mac.
Is Kaspersky Good
Thus far, Avast is still the only one I’ve found on the Mac to do on-by-default HTTPS scanning and to fail to check certificate validity.
Threatfire
Tags: Avast, man-in-the-middle, SSL